Business IntelligenceCloud ServicesIT Consulting & StrategySecurityTech Support & Managed IT ServicesTelecommunicationsConstructionEducationFinanceHealthcareLegalNon-ProfitsReal Estate
The constantly changing cyberthreats that we face require a constantly changing approach to how we deal with cybersecurity. It’s one of the reasons that we don’t recommend a set-it-and-forget approach. You need something that’s always adapting to the current threat landscape, not the way it looked six months ago.
As part of their attempt to keep up with cybercriminals, the Center for Internet Security (CIS) has updated its Critical Security Controls protocol to version 8.

What is CIS control V8?
CIS version 8 is an updated and revised version of the Critical Security Controls that CIS created back in 2013. These controls are a set of best practices and specific, actionable advice that cybersecurity professionals can use to help protect their businesses.
Version 8 reflects the current state of cybersecurity and provides businesses with a modified framework they can follow to help you break down your cybersecurity efforts into smaller, more manageable chunks. Among other things, breaking it down helps ensure that you’re following through on your plans to protect your assets.
What has changed in V8?
The biggest notable change that was made in V8 is that CIS reduced the number of controls from 20 down to 18, as you can see in the diagram below.
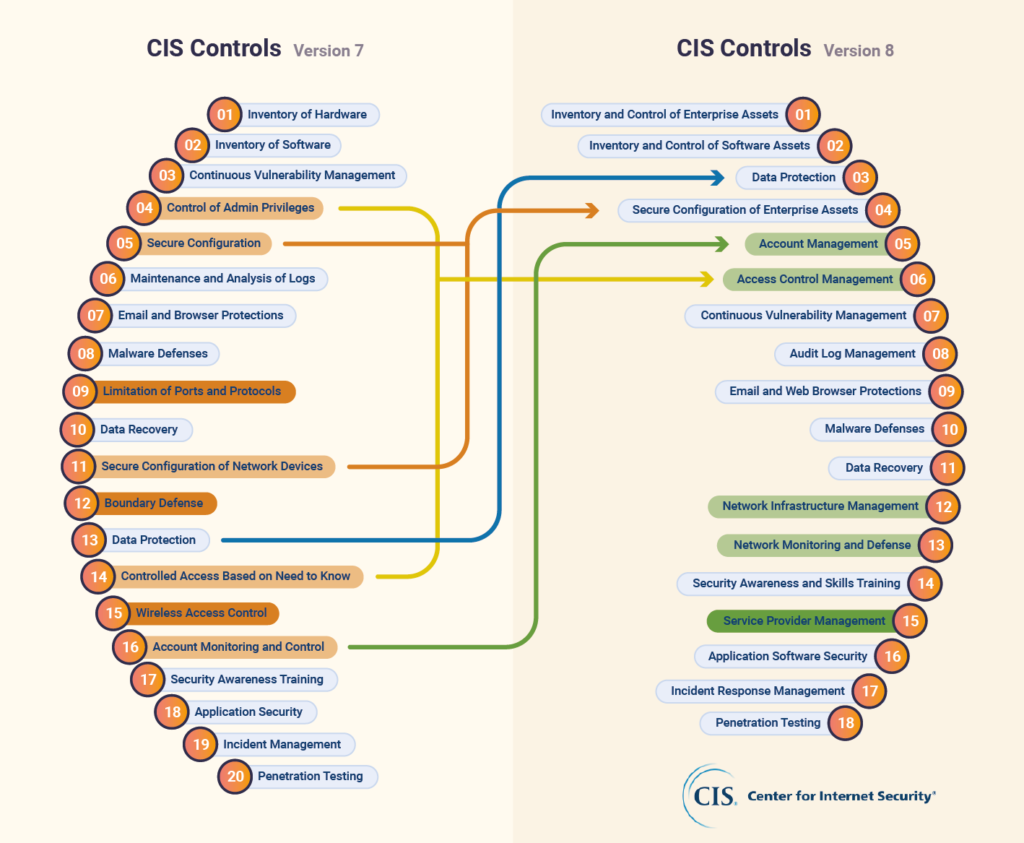
The reasoning behind this was that it helps organizations better understand and work with the framework. It’s not meant to be a rigid set of rules that you must follow for things to be successful. The goal instead is to create something that can be used in a flexible way that can be applied to all aspects of your cybersecurity efforts.
How does it fit into your cyber security plans?
CIS version 8 is meant to be a guide that helps you create a thorough list of recommendations from a wide range of sources that, when combined, protect your business from attacks.
Among other things, V8 helps you create a prioritized list of what you need to implement in your organization to ensure you’re not missing any critical components of your cybersecurity plan.
Ideally, you’d create implementation groups that focus on certain controls within the list. These implementation groups can take on smaller chunks of your security effort, which not only makes it easier to accomplish tasks (because we all know how easy it is for some of this stuff to get lost in development forever), but also makes it possible to create a solid foundation of security across your entire organization.
CIS Controls are not, it should be noted, a replacement for regulatory requirements, but rather a way to guide your security efforts to help keep you compliant and protected.
What is the framework of asset protection?
The CIS Controls framework is 18 controls that you follow to help map out your security requirements and implement them. The list of controls can be seen below.
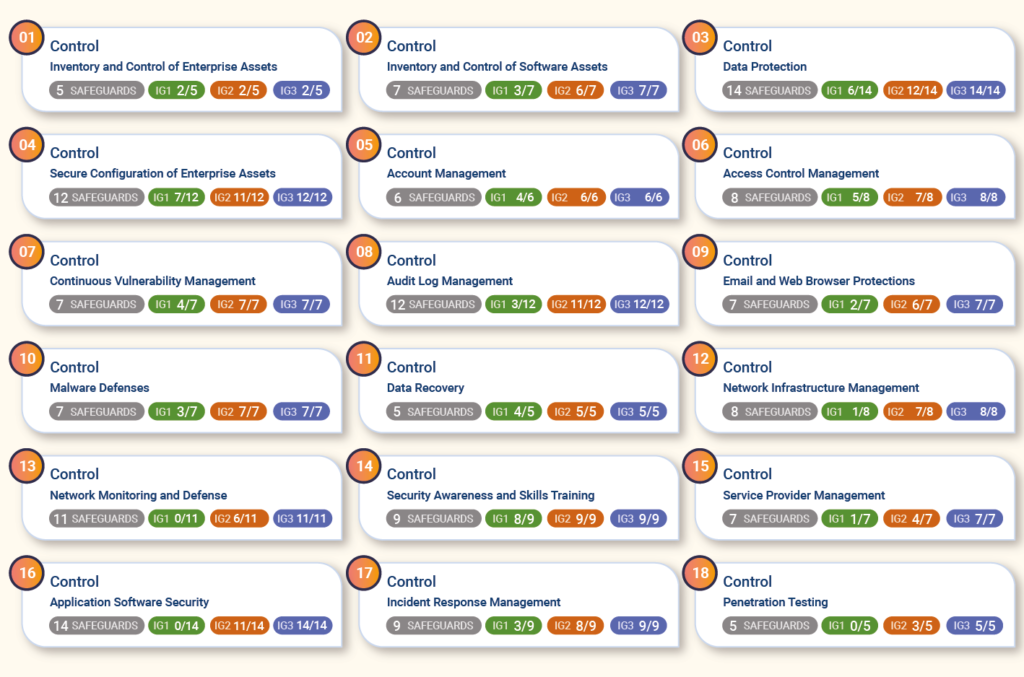
As CIS says, it’s not about following the list in order. The goal is to create a starting point for organizations and to help those who may not have the best security posture better understand what they should be focusing on.
The framework is free to download from the CIS website (here) and, once you’ve downloaded it, you have a comprehensive guide that not only walks you through the steps and helps you understand what you should be doing, but also take the time to explain why each control is important. For example, for the first control Inventory and Control of Enterprise Assets, they explain that you can’t protect your assets if you don’t know what you have. By taking the time to create a full inventory of all your assets, you reduce the risk that a persistent cybercriminal is going to find some long-forgotten asset that hasn’t been protected.
Once they explain the why, the framework goes on to tell you what tools you can use to ensure that you’re protected and what safeguards you can put in place.
Ultimately, you can use V8 to create a comprehensive set of procedures that help keep you safe, you learn what tools can help you, and you gain a deeper understanding of why you’re doing something. This reduces the likelihood of you (or someone on your team/in your organization) deciding certain things are unimportant or don’t need to be worried about.
Want help working with a more secure framework?
Even with a guide as thorough as the CIS Controls V8, keeping your business, data, and customers protected is a huge task. Attempting to take it on solo (or even as part of a working group) can often lead to things either being forgotten or implemented in a half-hearted way because other tasks have come along.
To help make sure this doesn’t happen, partnering with an organization of security-minded professionals (like us) can help. We have the training and expertise needed to help you work through the framework and implement the necessary protections for your business.
Contact us today to learn more.
 October 5, 2022
October 5, 2022 Manhattan Tech Support
Manhattan Tech Support




